What is XML-RPC?
An XML-based protocol called the XML-RPC is used to transmit data across a network between computer systems. Dave Winer created the XML-RC in 1998. Complex data structures can be communicated and processed using the XML-RPC protocol, which employs the HTTP transport standard. In this article we go through about How to stop a WordPress xml-rpc attack.
The primary purpose of XML-RPC is to unify various computing environments without the direct sharing of complex data structures. Through a network, XML-RPC makes it simple to establish faster computer-to-computer communication. Perl, Java, Python, C, C++, PHP, and numerous more programming languages all make use of XML-RPC.
You need an XMLRPC file access when a client manages any of the components of your WordPress website remotely. An HTTP-POST request is what an XML-RPC message actually is. There are some requests and responses where the body of the request is in XML format. On a server, a process runs this and returns a value. Additionally, this value will be in XML format. The parameters of the process can be scalars, strings, integers, etc.
What is Xmlrpc.php file and why should be disabled?
WordPress has a feature called XML-RPC that allows data to be transmitted using HTTP as the transport protocol and XML as the encoding format. Since WordPress is not a self-enclosed system, it occasionally needs to interact with other systems to complete a task. For instance, you can use the remote access capability made available by xmlrpc.php to post content to the website from a mobile device. This xmlrpc.php file implements trackbacks and pingbacks from other Jetpack plugin-related features as well as from other websites, allowing users to connect to the website via a smartphone.
A DDoS attack could have also resulted in the website being taken offline. Hackers will use the WordPress pingback capability to simultaneously ping thousands of websites. Therefore, this functionality in xmlrpc.php will enable hackers to launch a DDoS assault using a limitless supply of IP addresses.
But there could be security issues because of XML-PRC. The files that can be used to enable brute force assaults on the website, rather than XML-RPC itself, are the source of the security problem. The hacker will attempt to enter your website using the xmlprc.php file and numerous username and password combinations. They can test with hundreds of different passwords with just one command. They will be able to violate the security guidelines as a result, leading to a brute force attack.
How can we disable XML-RPC in WordPress on cPanel server?
XML-RPC validator is a tool that may be used to determine whether XML-RPC is active on your website. XML-RPC can be manually disabled on WordPress websites using File Manager in cPanel or with the help of plugins. Let’s look at the methods listed below to disable the XML-PRC file in cPanel.
Step 1: Login in your cPanel with a valid username and password.

Step 2: Navigate to file manager and go to root folder. Then access the folder ‘public_html’.
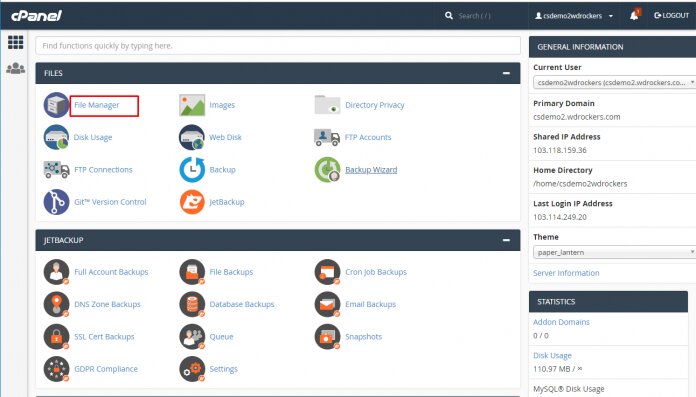
Step 3: Find the .htaccess file in the public_html directory or create a new .htaccess file. In case, you don’t see the file, it’s a hidden file and you need to change the settings to display hidden files by navigating to the gear button icon from the top-right corner.

Step 4: Once you find the .htaccess file, right-click on it and choose the Edit button.
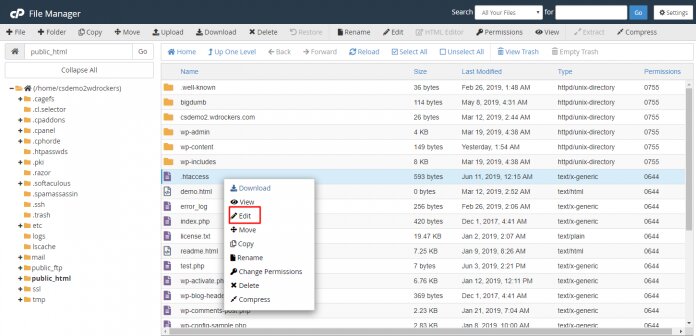
Step 5: After clicking the button you can see a new popup appears to allow you to disable encoding. Then click on the Edit button, and a new tab appears in the browser.

Step 6: Copy and Paste the below code in the .htaccess file.
#Block XML-RPC
<Files xmlrpc.php>
order deny,allow
deny from all
allow from // IP
</Files>
Also read, Advantages of creating website using WordPress
Your website will now totally disable the xmlrpc.php file. It will increase the security of your website and reduce security risks.